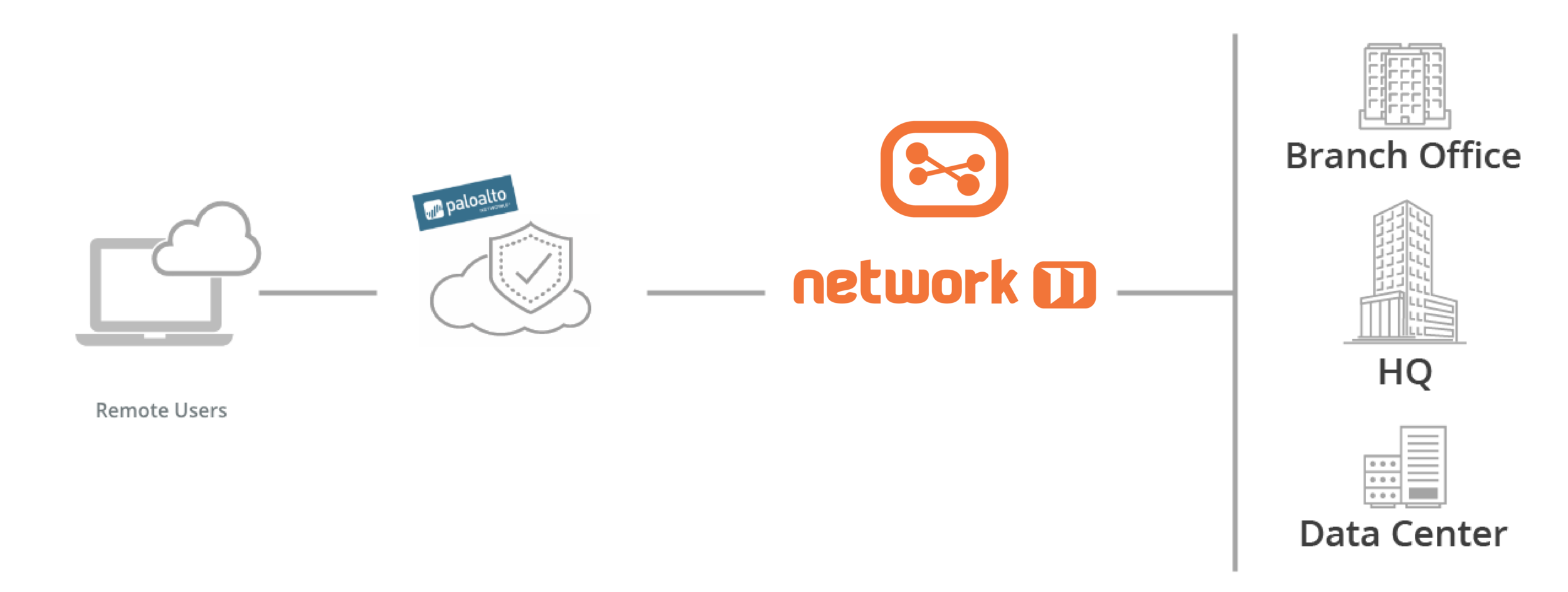
Network11’s managed SD-WAN security focuses on protecting the enterprise from breach, both against external attacks, and by hardening our managed SD-WAN offering.
The four components are:
North-south firewalling at the SD-WAN branch
East-west site-segmentation via our new Zones capability
Cloud-based security-as-a-service partners
Network11 private backbone protection
At the branch, an access firewall within the NAP, Global Network11’s Secure Access Service Edge (SASE), offers ‘north-south’ control. Global Network11 Zones extends this to the LAN with ‘east-west’ security, through site-segmentation with policy-based access. Together, the two capabilities segment WAN traffic to Global Network11 and internet, from LAN traffic, both internal and DMZ.
A third capability extends security into the cloud though Global Network11’s security partners, including Zscaler. As an example, an enterprise may consume Zscaler’s complementary cloud-based security-as-a-Service, with Global Network11 directing traffic appropriately. Alternatively, remote workers may access Global Network11 via Palo Alto’s Prisma Cloud Security Suite providing authentication and acceleration.
In parallel, the Global Network11 private core delivers partitioned connectivity to all enterprises, encrypting the data and protecting against DDoS attack. Within the branch, enterprises have access to Syslog and Netflow logging, and at the network level, the Global Network11 cloud portal provides a single pane of glass for service configuration, monitoring and health.
Managed security for the enterprise WAN, integrated with the Network11 platform
Powerful Zones capability for site segmentation
Best-in-class partners
for cloud-based
security-as-a-service
Branch Protection – Stateful Firewalling and Zones
The SD-WAN edge is often the first line of defense. Global Network11 provides advanced access security solutions that are built into our ANAP SD-WAN branch appliance, a Secure Access Service Edge (SASE), eliminating the need to procure and manage dedicated security hardware.
ANAP includes a virtual stateful firewall that delivers north-south access protection as well as a simplified insertion model with features that also condition the last mile against packet loss and latency.
The new Zones capability offers site-segmentation to secure east-west traffic within the branch. For example, internal corporate traffic routed to the Global Network11 backbone, public internet traffic, and DMZ traffic such as local application servers or Guest WiFi.
From the branch, traffic follows one of three paths –
Internal to the Global Network11 backbone and then to other sites, as well as SLA-driven access to IaaS, PaaS, and SaaS.
External over the internet via a cloud-based firewall or CASB.
Cloud Security for Internet Traffic
Connections to ‘secured’ business-critical SaaS is via the Global Network11 network, with direct connections to many of the most strategic SaaS providers. Connectivity to other SaaS providers is simplified by directing traffic to a cloud-based security-as-a-service offering such as Zscaler.
The combined solution does not require additional on-premises hardware, appliances, or software, and is easy and cost-effective to deploy and manage.
Palo Alto’s Prisma Cloud Security Suite extends the protection of its next-generation security platform by leveraging a cloud-based security infrastructure for global enterprises to create and deploy consistent security policies across the entire organization.
Symantec Web Security Services ensures a full suite of threat protection and prevention applied to enterprise traffic from each site. Businesses enjoy direct Internet and cloud access with a consistent security layer without having to deploy separate technologies at each location.
Remote Access and Acceleration into the Global Network11 Managed SD-WAN
Enterprises with remote workers requiring access to the SD-WAN may easily connect via the Palo Alto’s Prisma Cloud Security Suite for authentication and acceleration. Global Network11 has partnered with Palo Alto for this capability.
Global Networkk11 Core Private Transport Network Protection
The Global Network11 delivers true multi-tenant data partitioning though virtualized compute, network, and storage resources. The resulting private backbone is more secure than competing MPLS services where customer traffic is not encrypted. This includes dedicated PoPs located in secured data centers, dedicated Layer 2 links, encryption with IPSec, key management, and DDoS protection. We manage this via a sophisticated orchestration platform, to ensure that your users have assured access to your vital applications and data, anywhere, and at any time.
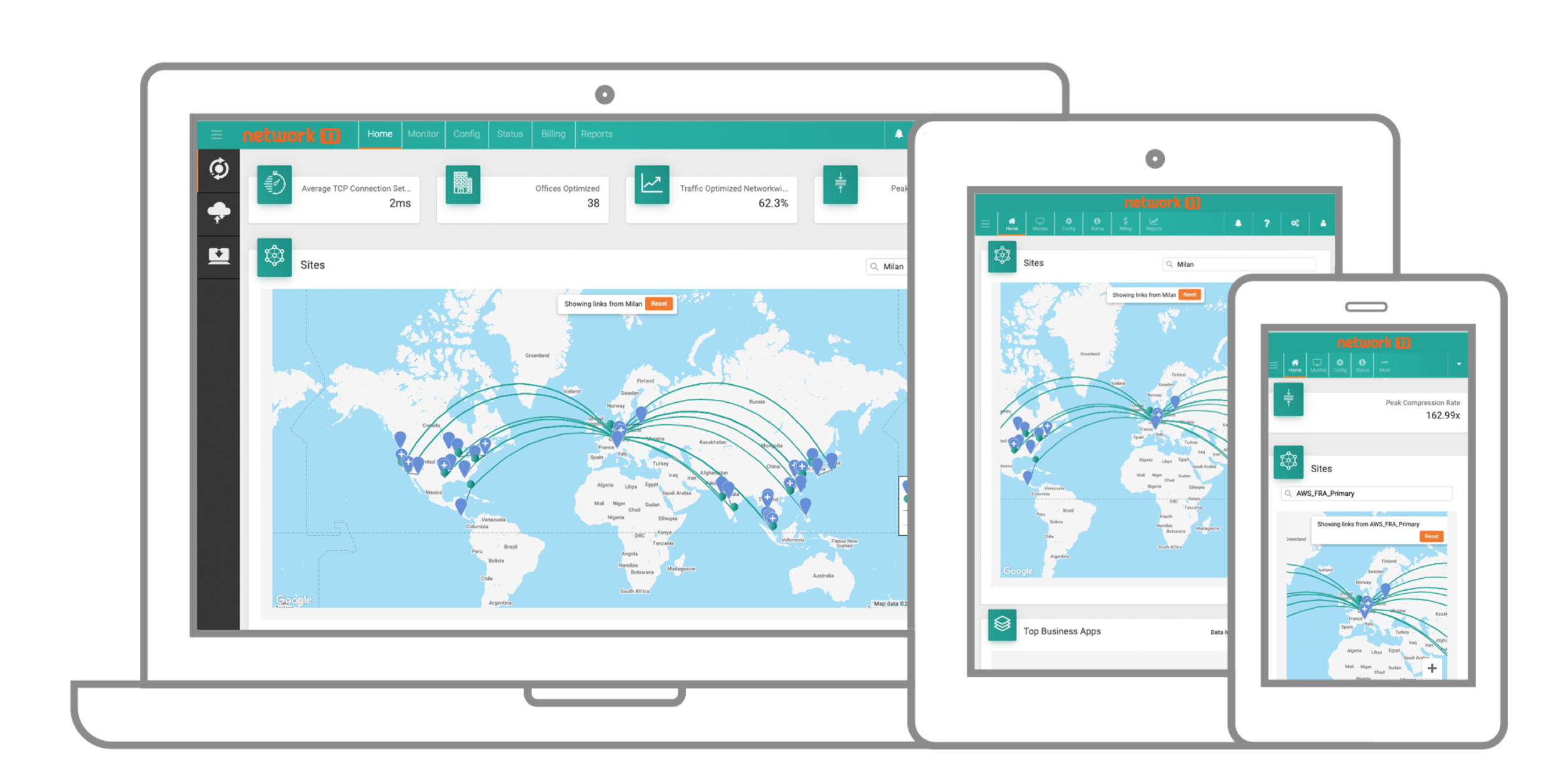
Network11 Portal: Early Warning Visibility Portal
Since all enterprise traffic goes through Global Network11’s global private network, including all on-premises and cloud applications, the Network11 portal provides unique visibility into all global users’ and locations’ network and application traffic.
Global Network11 enables IT for the first time to see holistic and specific data on all connections, applications, users, and locations globally, along with deep insight into both legit and suspicious network and application user activity. This provides an early warning system for IT to potentially pinpoint, identify, and stop security threats before they become massive issues. This is particularly useful for zero-day vulnerabilities and attacks that can sometimes evade certain security controls.
For example, an IT manager can see hundreds of connections from one or two regions with 0k or 1k traffic. Identifying as a potential beginning of a DDoS attack. This gives IT an opportunity to examine these endpoints for malware, clean them, and stop DDoS attack at the origination point before it even hits global communication channels, costing company business disruption, and additional expenses.